High quality Cisco CCNA Cyber Ops 210-250 dumps vce youtube update free shared. The best and most updated latest Cisco CCNA Cyber Ops https://www.leads4pass.com/210-250.html dumps exam training resources in PDF format free download from lead4pass. “Understanding Cisco Cybersecurity Fundamentals” is the name of Cisco CCNA Cyber Ops 210-250 exam dumps which covers all the knowledge points of the real Cisco exam.
Cisco CCNA Cyber Ops 210-250 dumps exam preparation kit contains all the necessary 210-250 questions that you need to know 210-250 SECFND – Cisco. You can download Cisco CCNA Cyber Ops 210-250 dumps pdf training material from lead4pass and pass the Cisco 210-250 exam in the first attempt. The best useful Cisco CCNA 200-125 dumps real exam answers update Cisco 200-125 dumps vce youtube demo. Download the best useful Cisco CCNA Cyber Ops 210-250 dumps vce software online to have a free try.

Google drive Cisco 210-250 dumps pdf materials: https://drive.google.com/open?id=0B_7qiYkH83VRaF8zb0JFVmRVclU
Google drive Cisco 210-255 dumps pdf materials: https://drive.google.com/open?id=0B_7qiYkH83VRTTJsYkV3c2xZb2s
Cisco CCNA Cyber Ops 210-250 Dumps Newest Question And Answers (1-30)
QUESTION 1
What is PHI?
A. Protected HIPAA information
B. Protected health information
C. Personal health information
D. Personal human information
Correct Answer: B
QUESTION 2
Which of the following are Cisco cloud security solutions?
A. CloudDLP
B. OpenDNS
C. CloudLock
D. CloudSLS
Correct Answer: BC
QUESTION 3
Which evasion method involves performing actions slower than normal to prevent detection?
A. traffic fragmentation
B. tunneling
C. timing attack
D. resource exhaustion
Correct Answer: C
QUESTION 4
Which encryption algorithm is the strongest?
A. AES
B. CES
C. DES
D. 3DES
Correct Answer: A
QUESTION 5
What is a trunk link used for?
A. To pass multiple virtual LANs
B. To connect more than two switches
C. To enable Spanning Tree Protocol
D. To encapsulate Layer 2 frames
Correct Answer: A
QUESTION 6
Which type of exploit normally requires the culprit to have prior access to the target system?
A. local exploit
B. denial of service
C. system vulnerability
D. remote exploit
Correct Answer: A
QUESTION 7
Which security monitoring data type is associated with application server logs? 210-250 dumps
A. alert data
B. statistical data
C. session data
D. transaction data
Correct Answer: D
QUESTION 8
Which network device is used to separate broadcast domains?
A. router
B. repeater
C. switch
D. bridge
Correct Answer: A
QUESTION 9
Which term represents a weakness in a system that could lead to the system being comp
A. vulnerability
B. threat
C. exploit
D. risk
Correct Answer: A
QUESTION 10
Which option is an advantage to using network-based anti-virus versus host-based anti- virus?
A. Network-based has the ability to protect unmanaged devices and unsupported operating systems.
B. There are no advantages compared to host-based antivirus.
C. Host-based antivirus does not have the ability to collect newly created signatures.
D. Network-based can protect against infection from malicious files at rest.
Correct Answer: D
QUESTION 11
Which two protocols are used for email (Choose two )
A. NTP
B. DNS
C. HTTP
D. IMAP
E. SMTP
Correct Answer: DE
QUESTION 12
At which OSI layer does a router typically operate?
A. Transport
B. Network
C. Data link
D. Application
Correct Answer: B
QUESTION 13
While viewing packet capture data, you notice that one IP is sending and receiving traffic for multiple devices by modifying the IP header, Which option is making this behavior possible?
A. TOR
B. NAT
C. encapsulation
D. tunneling
Correct Answer: B
QUESTION 14
Which option is a purpose of port scanning?
A. Identify the Internet Protocol of the target system.
B. Determine if the network is up or down
C. Identify which ports and services are open on the target host.
D. Identify legitimate users of a system.
Correct Answer: C
QUESTION 15
An intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources. Which evasion technique does this attempt indicate?
A. traffic fragmentation
B. resource exhaustion
C. timing attack
D. tunneling
Correct Answer: B
QUESTION 16
Which of the following is true about heuristic-based algorithms?
A. Heuristic-based algorithms may require fine tuning to adapt to network traffic and minimize the possibility of false positives.
B. Heuristic-based algorithms do not require fine tuning.
C. Heuristic-based algorithms support advanced malware protection.
D. Heuristic-based algorithms provide capabilities for the automation of IPS signature creation and tuning.
Correct Answer: A
QUESTION 17
Which security principle states that more than one person is required to perform a critical task?
A. due diligence
B. separation of duties
C. need to know
D. least privilege
Correct Answer: B
QUESTION 18
Which tool is commonly used by threat actors on a webpage to take advantage of the software vulnerabilities of a system to spread malware? 210-250 dumps
A. exploit kit
B. root kit
C. vulnerability kit
D. script kiddie kit
Correct Answer: A
QUESTION 19
If a web server accepts input from the user and passes it to a bash shell, to which attack method is it vulnerable?
A. input validation
B. hash collision
C. command injection
D. integer overflow
Correct Answer: C
QUESTION 20
Based on which statement does the discretionary access control security model grant or restrict access ?
A. discretion of the system administrator
B. security policy defined by the owner of an object
C. security policy defined by the system administrator
D. role of a user within an organization
Correct Answer: B
QUESTION 21
Which definition of the virtual address space for a Windows process is true?
A. actual physical location of an object in memory
B. set of virtual memory addresses that it can use
C. set of pages that are currently resident in physical memory
D. system-level memory protection feature that is built into the operating system
Correct Answer: B
QUESTION 22
How many broadcast domains are created if three hosts are connected to a Layer 2 switch in full-duplex mode?
A. 4
B. 3
C. None
D. 1
Correct Answer: D
QUESTION 23
Which hashing algorithm is the least secure?
A. MD5
B. RC4
C. SHA-3
D. SHA-2
Correct Answer: A
QUESTION 24
What is one of the advantages of the mandatory access control (MAC) model?
A. Stricter control over the information access.
B. Easy and scalable.
C. The owner can decide whom to grant access to.
Correct Answer: B
QUESTION 25
Which definition of vulnerability is true?
A. an exploitable unpatched and unmitigated weakness in software
B. an incompatible piece of software
C. software that does not have the most current patch applied
D. software that was not approved for installation
Correct Answer: A
QUESTION 26
Which definition of a process in Windows is true?
A. running program
B. unit of execution that must be manually scheduled by the application
C. database that stores low-level settings for the OS and for certain applications
D. basic unit to which the operating system allocates processor time
Correct Answer: A
QUESTION 27
210-250 dumps According to the attribute-based access control (ABAC) model, what is the subject location considered?
A. Part of the environmental attributes
B. Part of the object attributes
C. Part of the access control attributes
D. None of the above
Correct Answer: A
QUESTION 28
Which term represents a potential danger that could take advantage of a weakness in a system?
A. vulnerability
B. risk
C. threat
D. exploit
Correct Answer: B
QUESTION 29
DRAG DROP
Drag the technology on the left to the data type the technology provides on the right.
Select and Place:
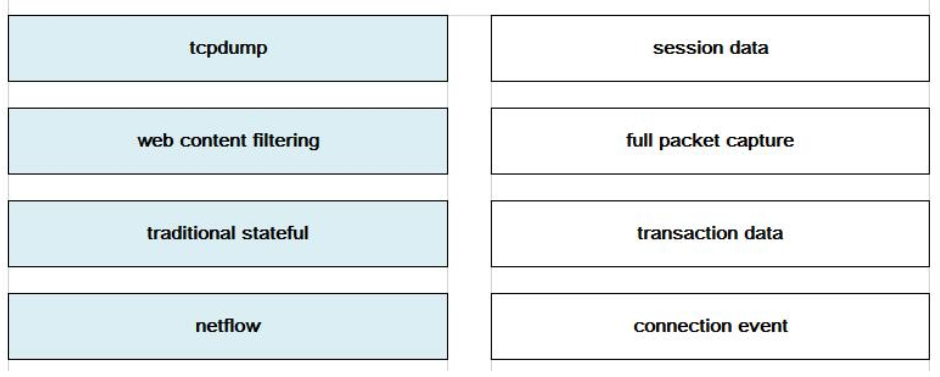
Correct Answer:
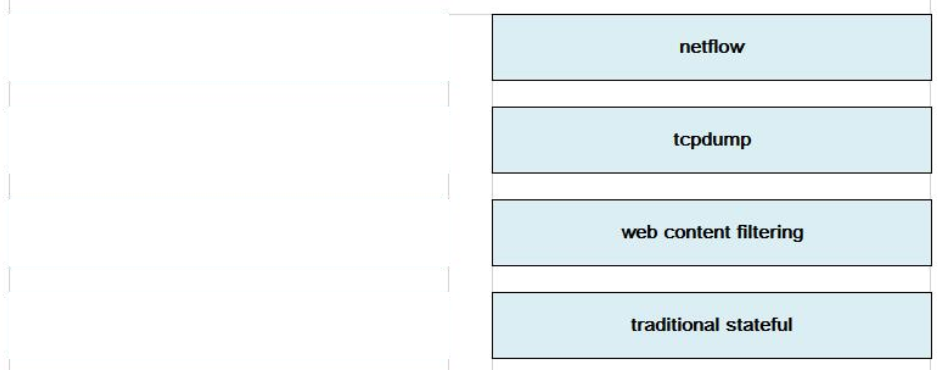
QUESTION 30
DRAG DROP
Drag the data source on the left to the left to the correct data type on the right.
Select and Place:
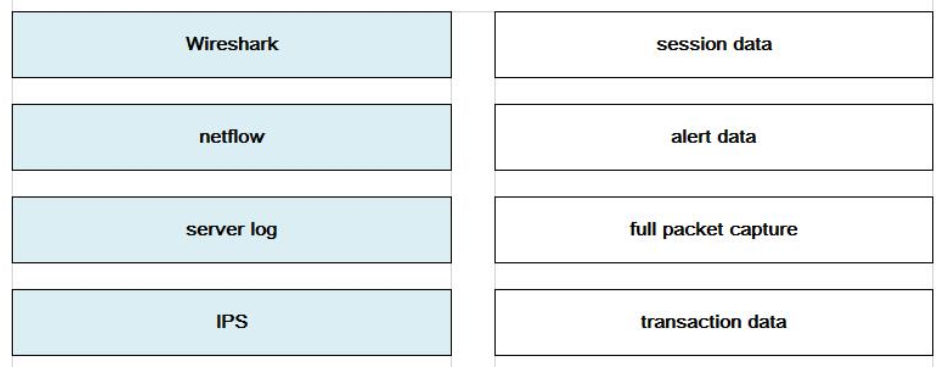
Correct Answer:
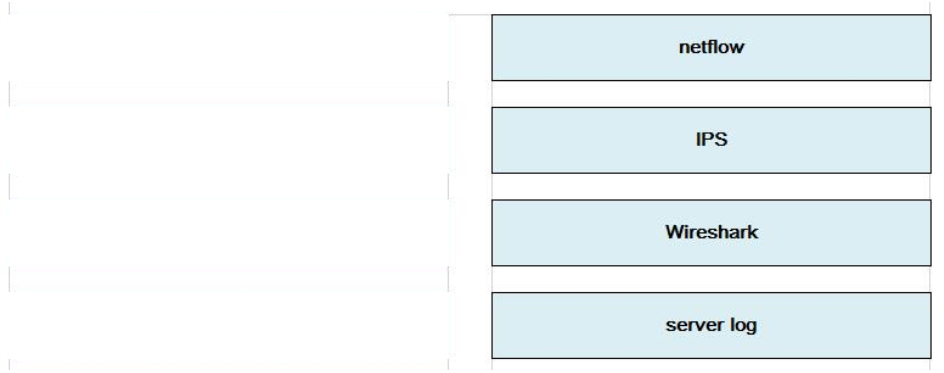
Google drive Cisco 210-250 dumps pdf materials: https://drive.google.com/open?id=0B_7qiYkH83VRaF8zb0JFVmRVclU
Google drive Cisco 210-255 dumps pdf materials: https://drive.google.com/open?id=0B_7qiYkH83VRTTJsYkV3c2xZb2s
Prepare for Cisco 210-250 exam with best Cisco CCNA Cyber Ops 210-250 dumps pdf practice files and study guides download free try from lead4pass. Helpful newest Cisco CCNA Cyber Ops https://www.leads4pass.com/210-250.html dumps pdf training resources which are the best for clearing 210-250 exam test, and to get certified by Cisco CCNA Cyber Ops.
Latest Cisco CCNA Cyber Ops 210-250 dumps vce youtube:
https://youtu.be/Qha0fEQ3n7M